Challenge Description
From the description, it seems like this challenge will be using both Forensics and Cryptography concepts.
As usual, we start off by downloading the image using wget <link>.
Contents of the file
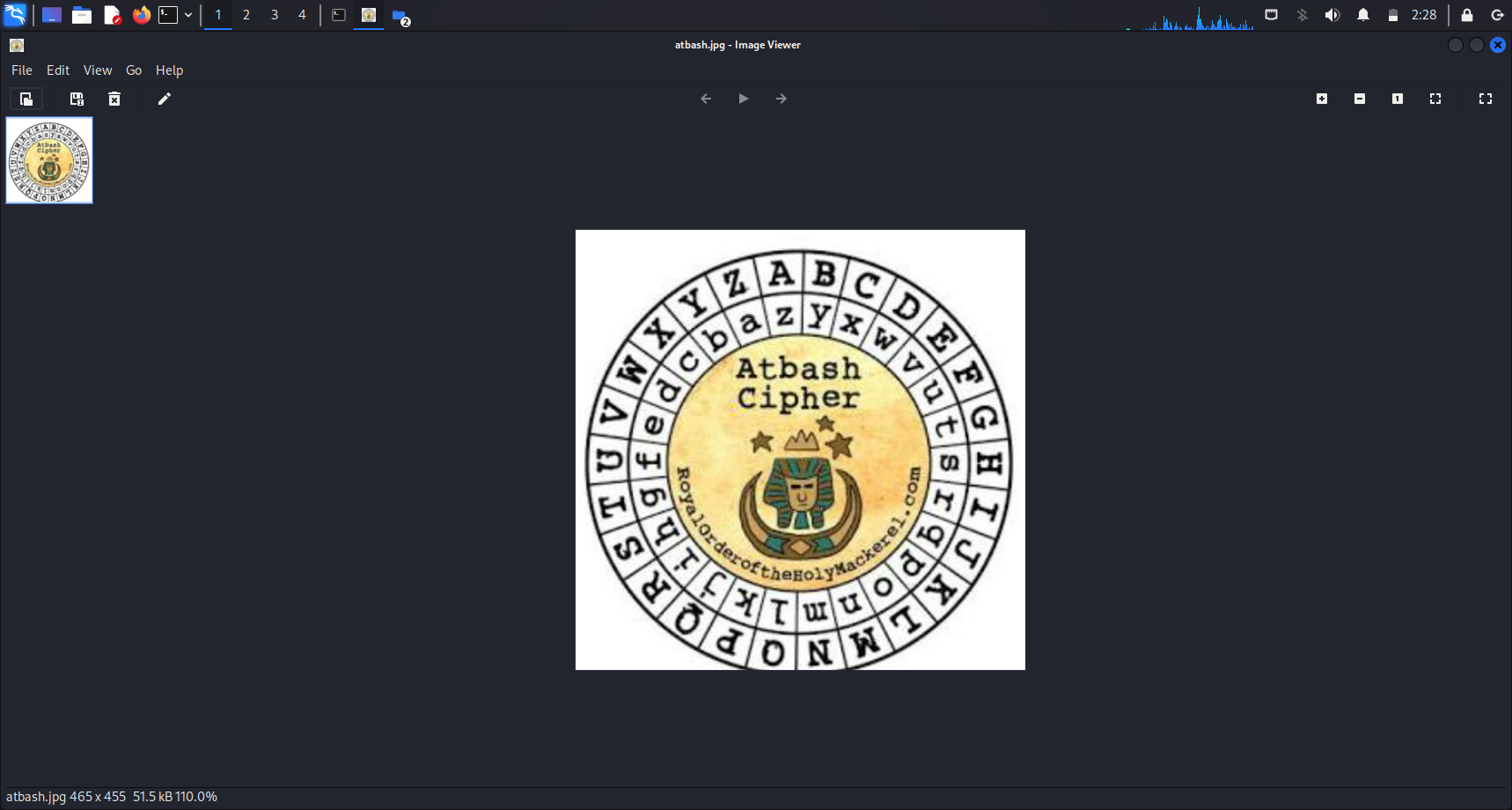
After opening the file, we now know that the flag is likely encrypted using the Atbash Cipher. However, this was the only file we were provided with.
PicoCTF Hint: Download the image and try to extract it.
Attempts to extract the hidden files
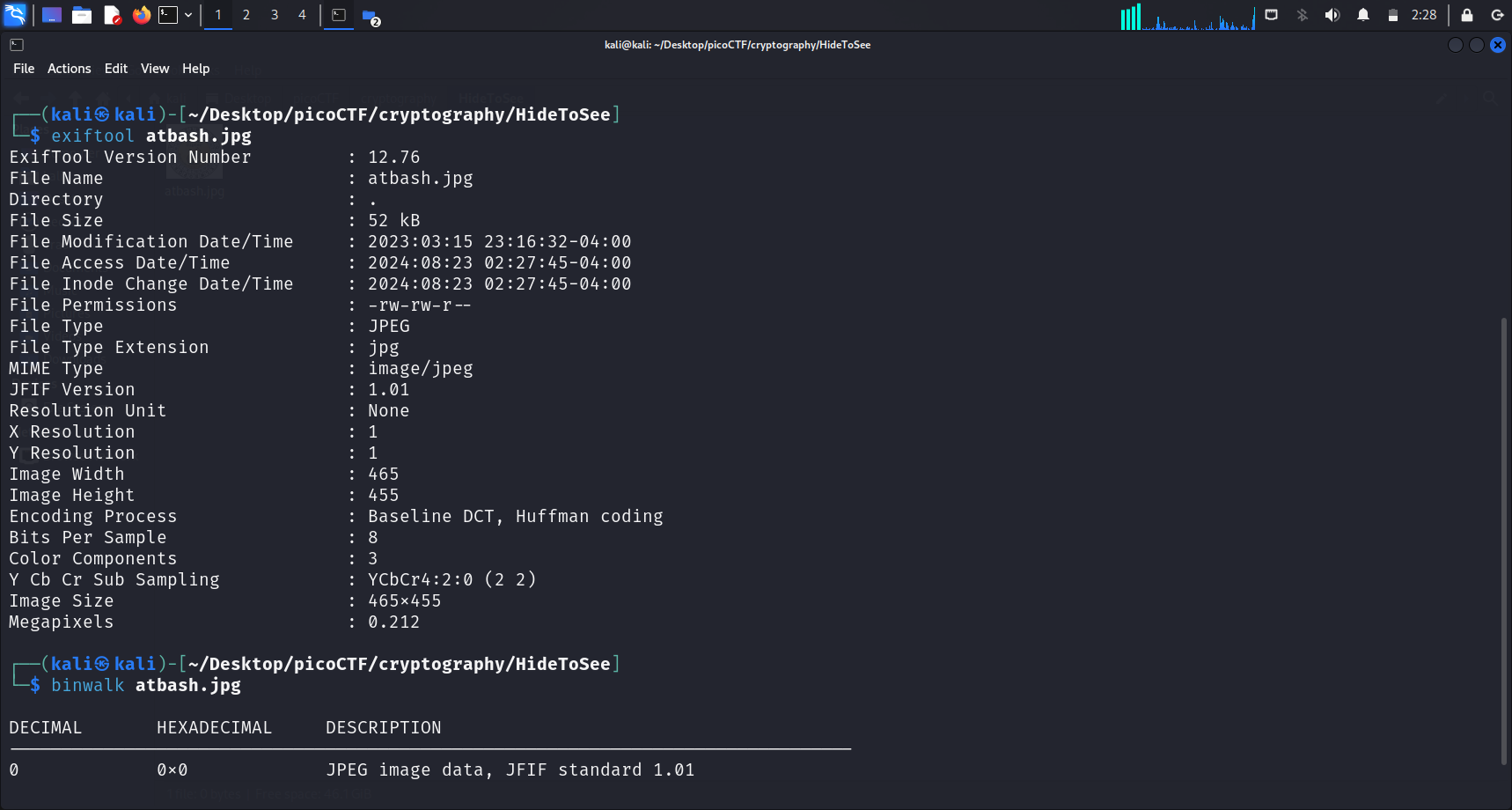
Failed Attempts
Running
exiftoolandbinwalkto get a better understanding of the file was not useful. They did not provide me with any clue to proceed.
However, since we are tasked to extract hidden files, I tried using Stegseek.
Stegseek
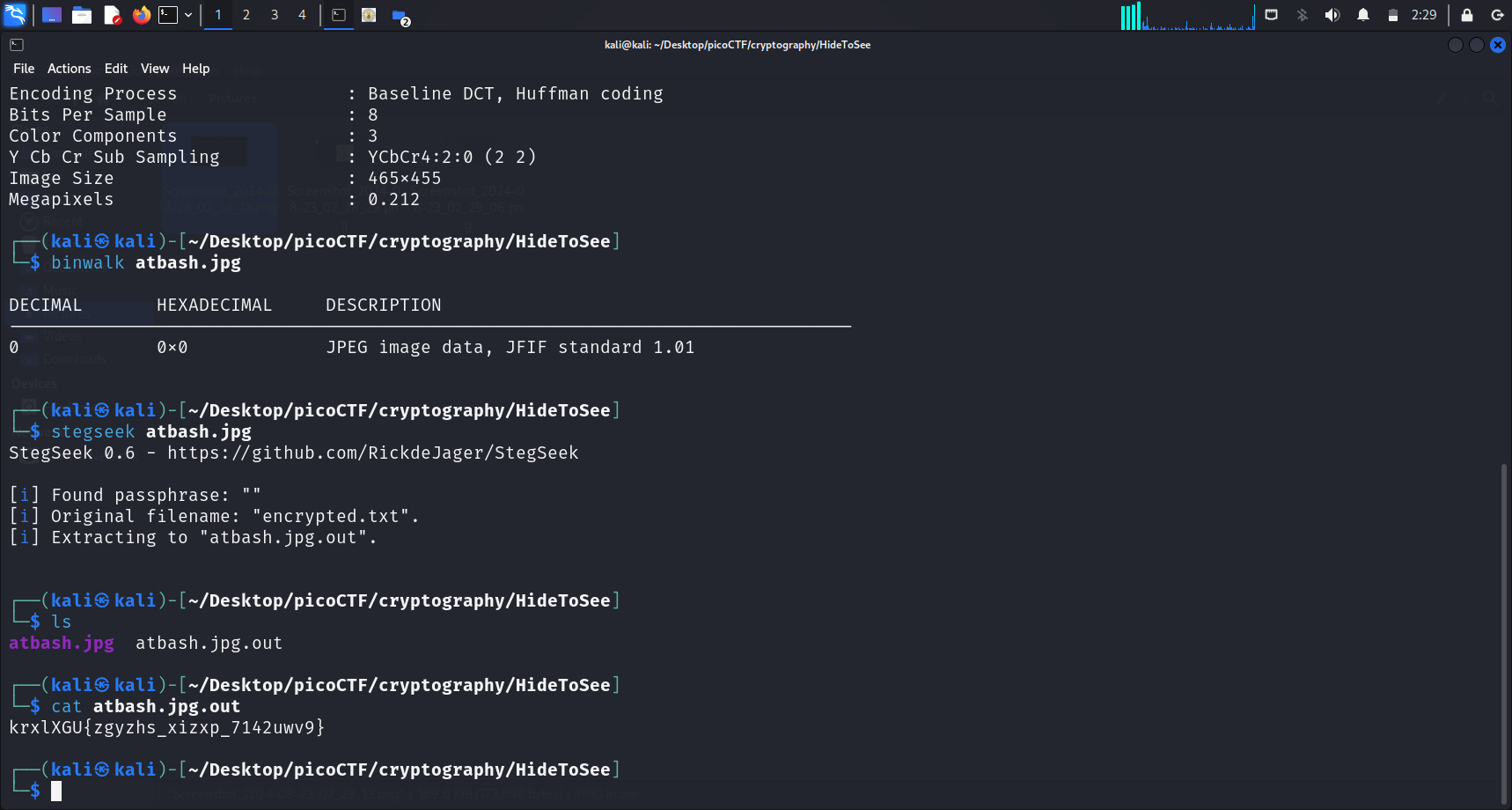
Running stegseek was successful, and now we have extracted a file from the original image. We can proceed by doing cat <file-name> to check its contents.
Encrypted Flag
This string,
krxlXGU{zgyzhs_xizxp_7142uwv9}, was displayed when thecatcommand was executed.
Getting the Flag
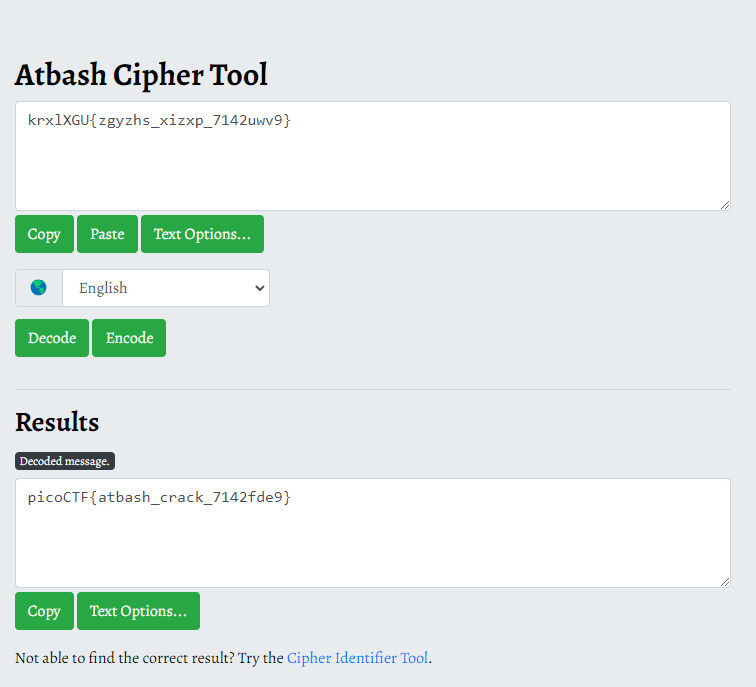
We can simply use an online Atbash Cipher tool to decrypt the flag. I used this, but CyberChef works just as well.
Flag
picoCTF{atbash_crack_7142fde9}