Challenge Description
Seems like a typical network forensics challenge. After downloading the pcap file using wget, we can use Wireshark to get the flag.
Wireshark
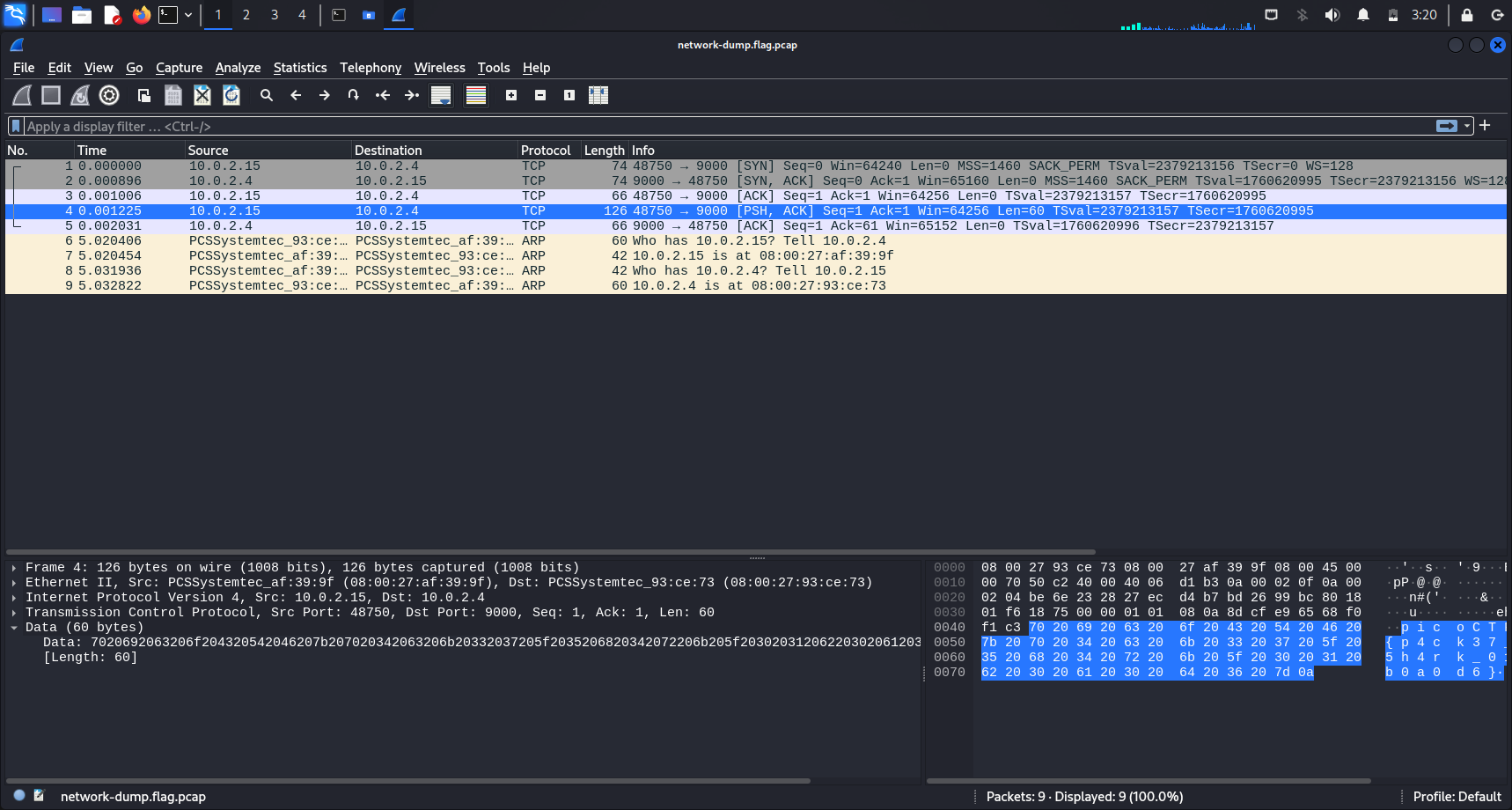
Since there are only 9 packets in this pcap file, finding the flag was straightforward. Display filters was not necessary.
Using strings
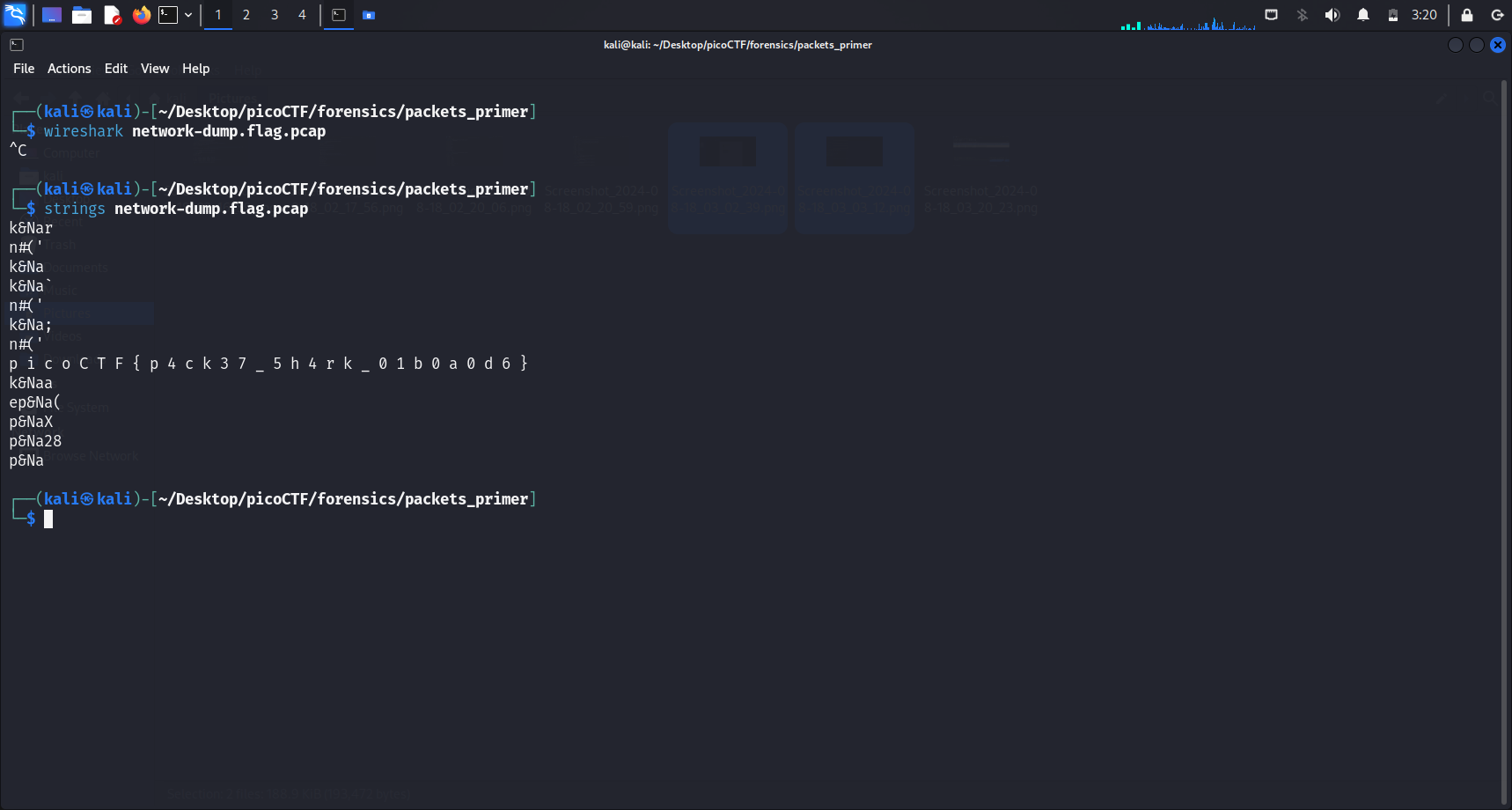
strings also works here. The flag is revealed instantaneously.
For both methods, all we have to do after that is just formatting the flag, that is, removing the redundant spaces in between the characters.
Flag
picoCTF{p4ck37_5h4rk_01b0a0d6}