Challenge Description
We shall start our journey by downloading the file using wget <link>. The downloaded file is a .pcap file. Hence we will continue by using Wireshark.
The capture.pcap file contained a total of 2317 packets. After checking the Protocol Hierarchy, I decided to use UDP as a display filter, and proceeded by following a random UDP stream.
PicoCTF Hint: What are streams?
This confirms that we should pay more attention to the
streamsin Wireshark.
Finding the flag
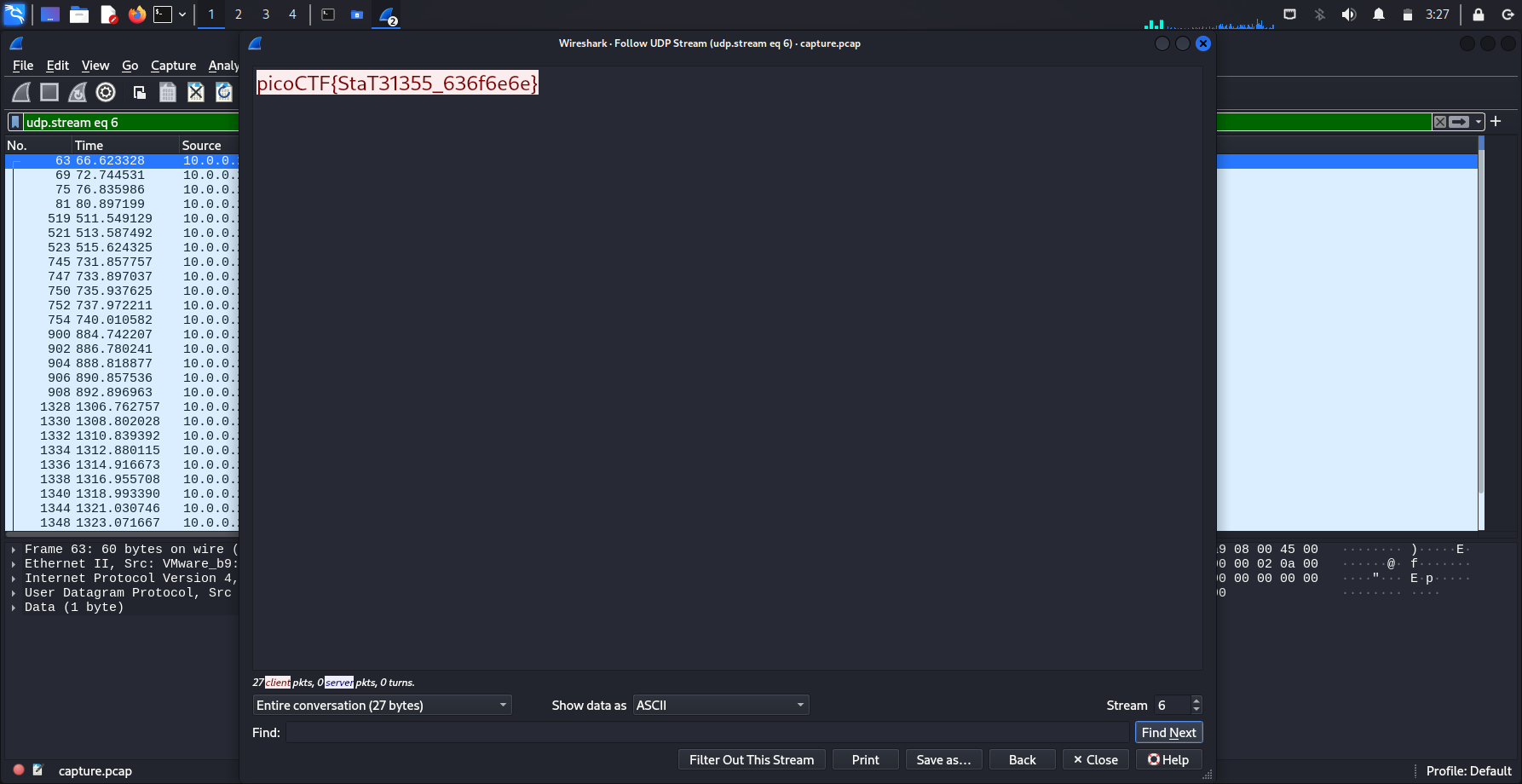
I analysed the various UDP streams, and managed to find the flag in the 6th stream.
Decoy Flags
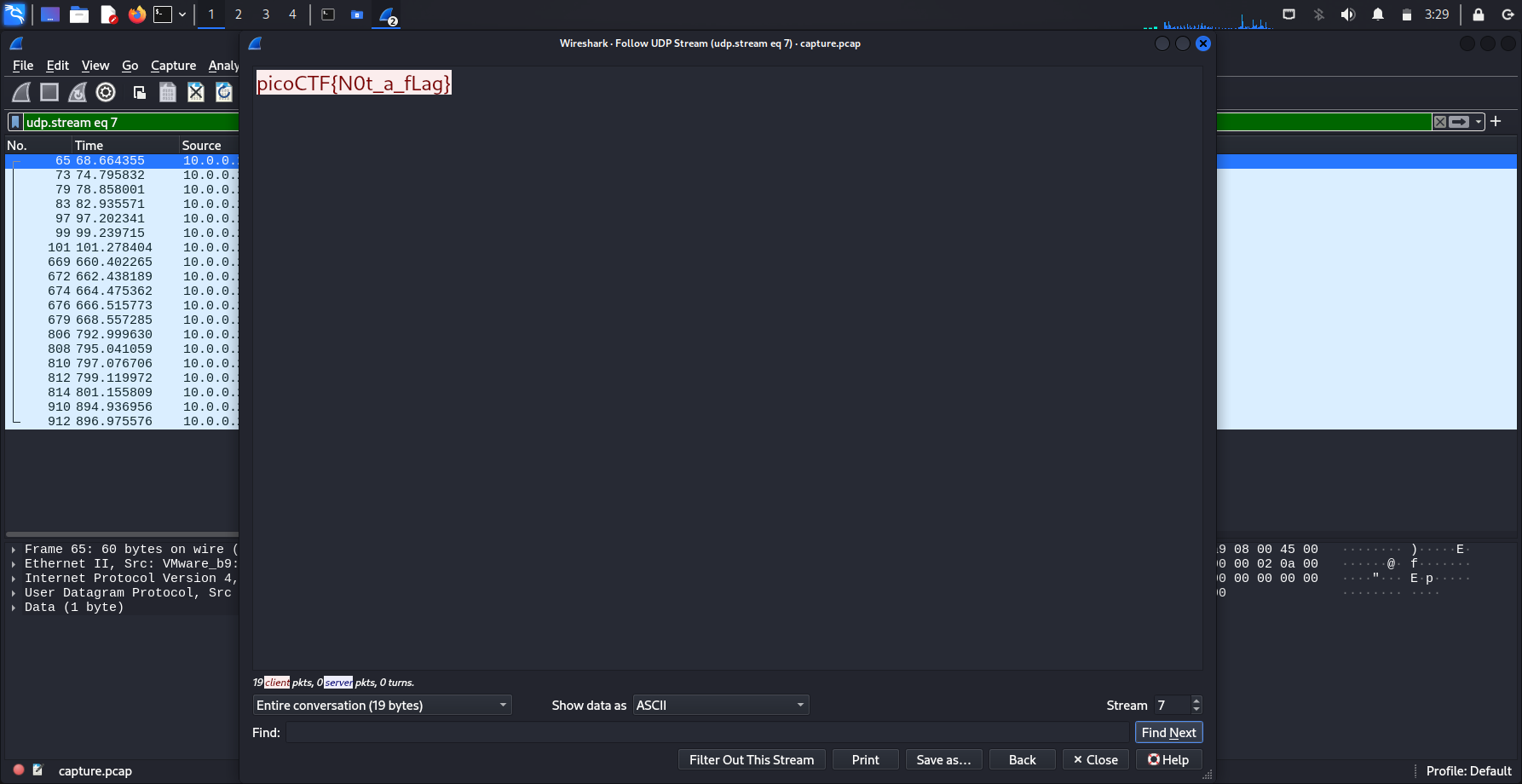
There are decoy flags in this challenge, such as one fake flag in UDP 7th stream.
Flag
picoCTF{StaT31355_636f6e6e}