Challenge Description
We will first download and extract the compressed disk image using wget <link> and gunzip <file-name> respectively. We will then need to use The Sleuth Kit (TSK) commands for disk image analysis.
Linux File System
Having a basic knowledge about the Linux Directory Structure will be helpful for this challenge.
mmls command
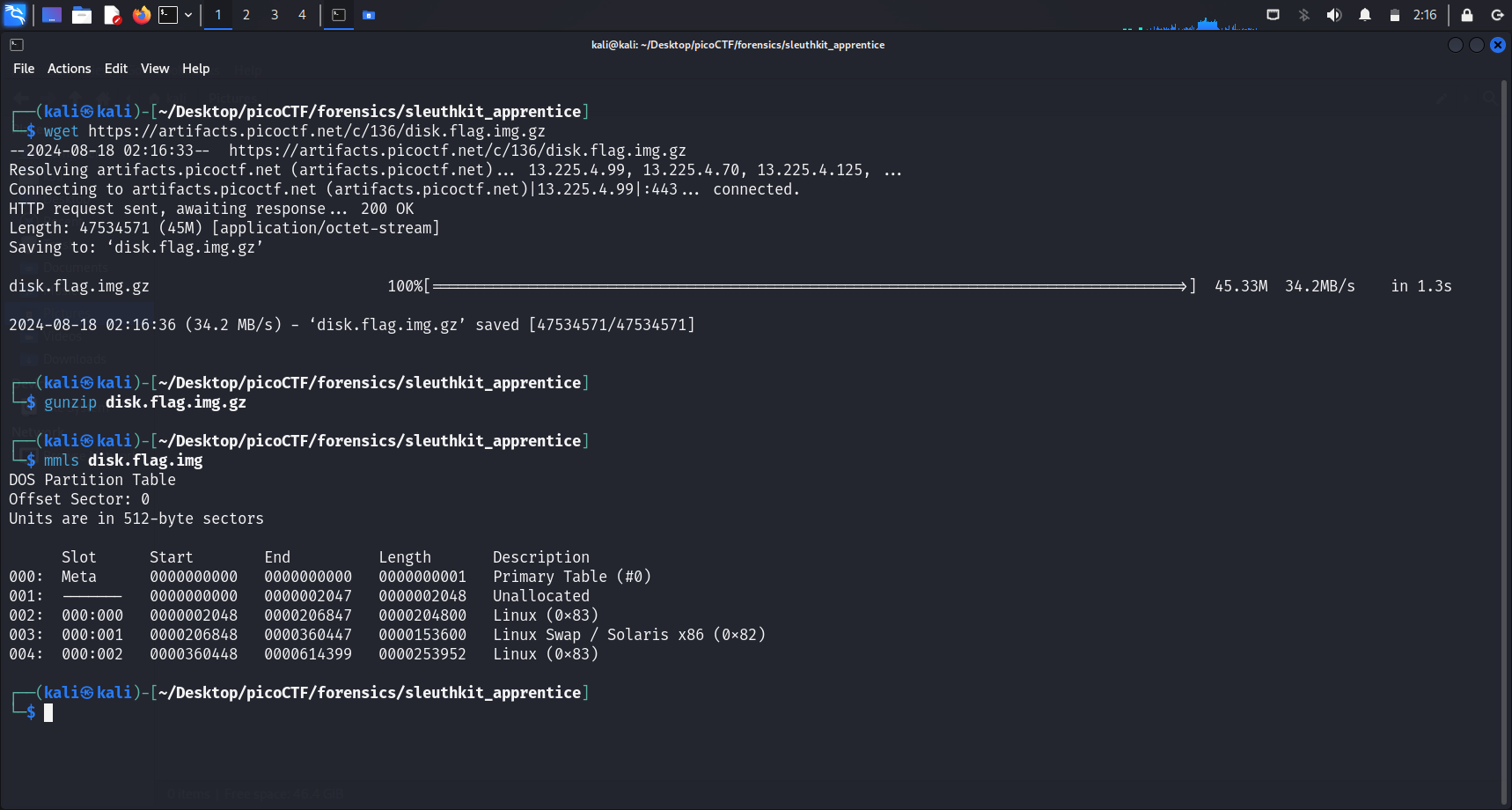 Next, we run
Next, we run mmls to display the partition layout of a volume system (partition tables). This will provide us with the offset address for each partition on the image, which will be useful later.
Offset address
This is basically the starting address of each partition.
mmls <image-name>will highlight theStartof each partition.
fsstat command
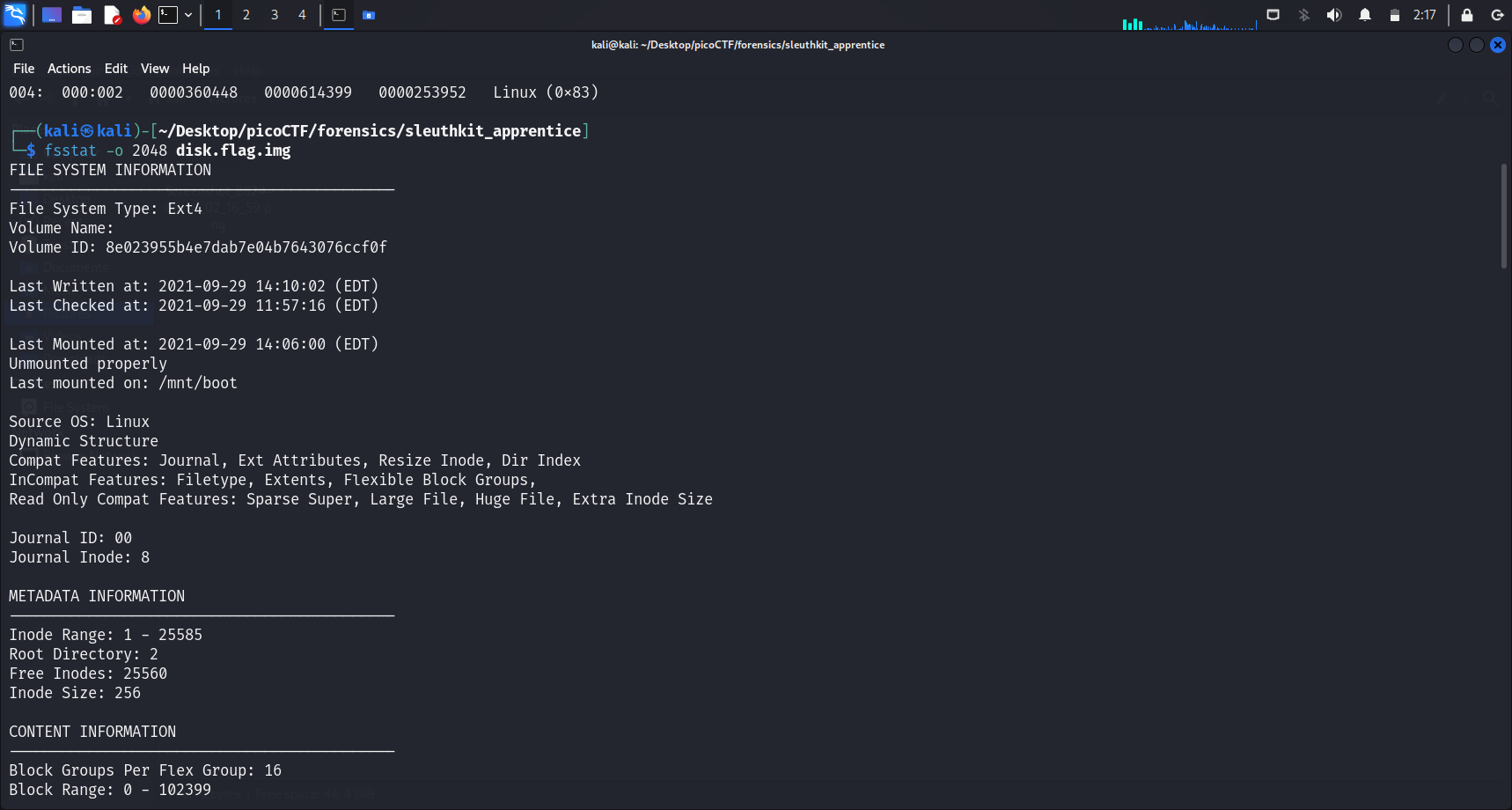
To get more information about the different partitions, we can do fsstat. fsstat will display the general details of a file system.
Usage of
fsstat
fsstat -o <img-offset> <image-name>The<img-offset>is the sector offset where the file system starts in the image.
For this challenge, fsstat was not particularly useful, so I went on to attempt fls.
fls command
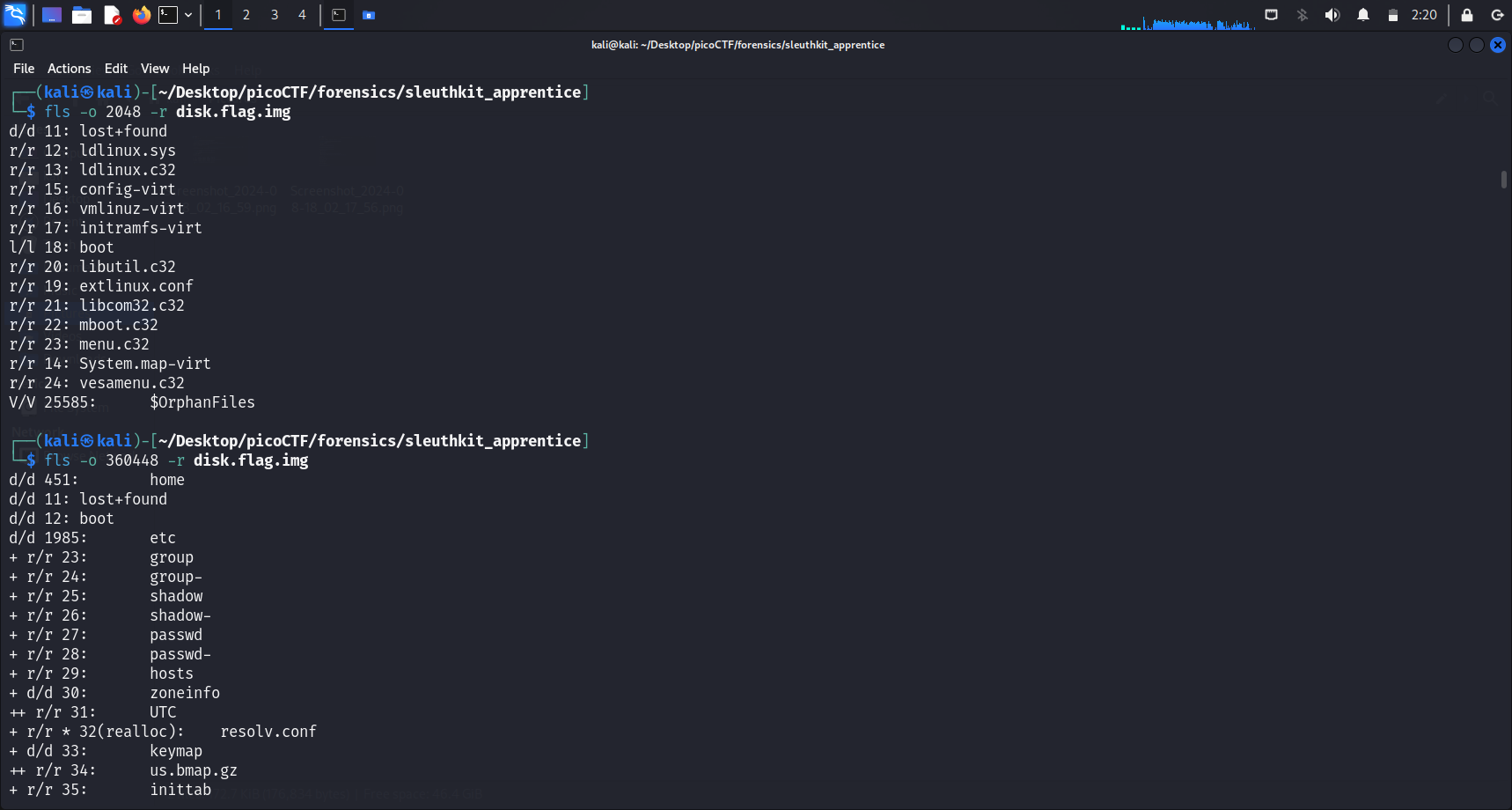 The
The fls command lists file and directory names in a disk image. I used the -r flag to search recursively for files and directories in each partition as well.
There wasn’t much that seemed of interest on the first partition. However when I ran the same command on the third partition, it revealed a lot of files and directories present in this partition.
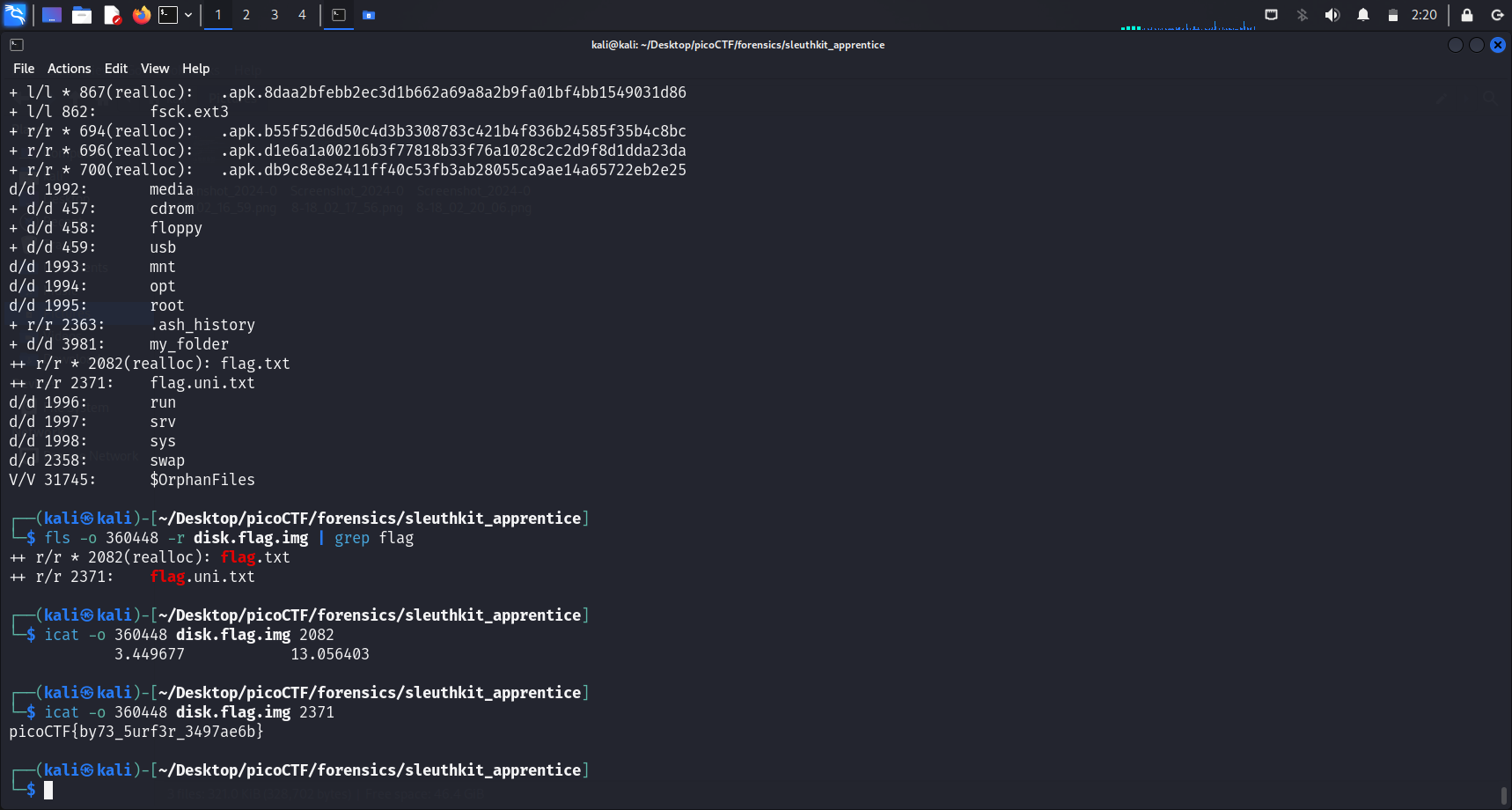
I then ran fls -o 360448 -r disk.flag.img | grep flag and found 2 .txt files in this partition. Subsequently, I tried icat on both files and obtained the flag.
Usage of
icat
icatis used to output the contents of a file based on its inode numbericat -o <img-offset> <image-name> <inode-number>Specifying the partition offset and the inode number as such allows the content of file to be displayed.
Flag
picoCTF{by73_5urf3r_3497ae6b}