Challenge Description
After downloading the file, we realise that it is a pcap file, as the challenge name already suggests.
Using strings
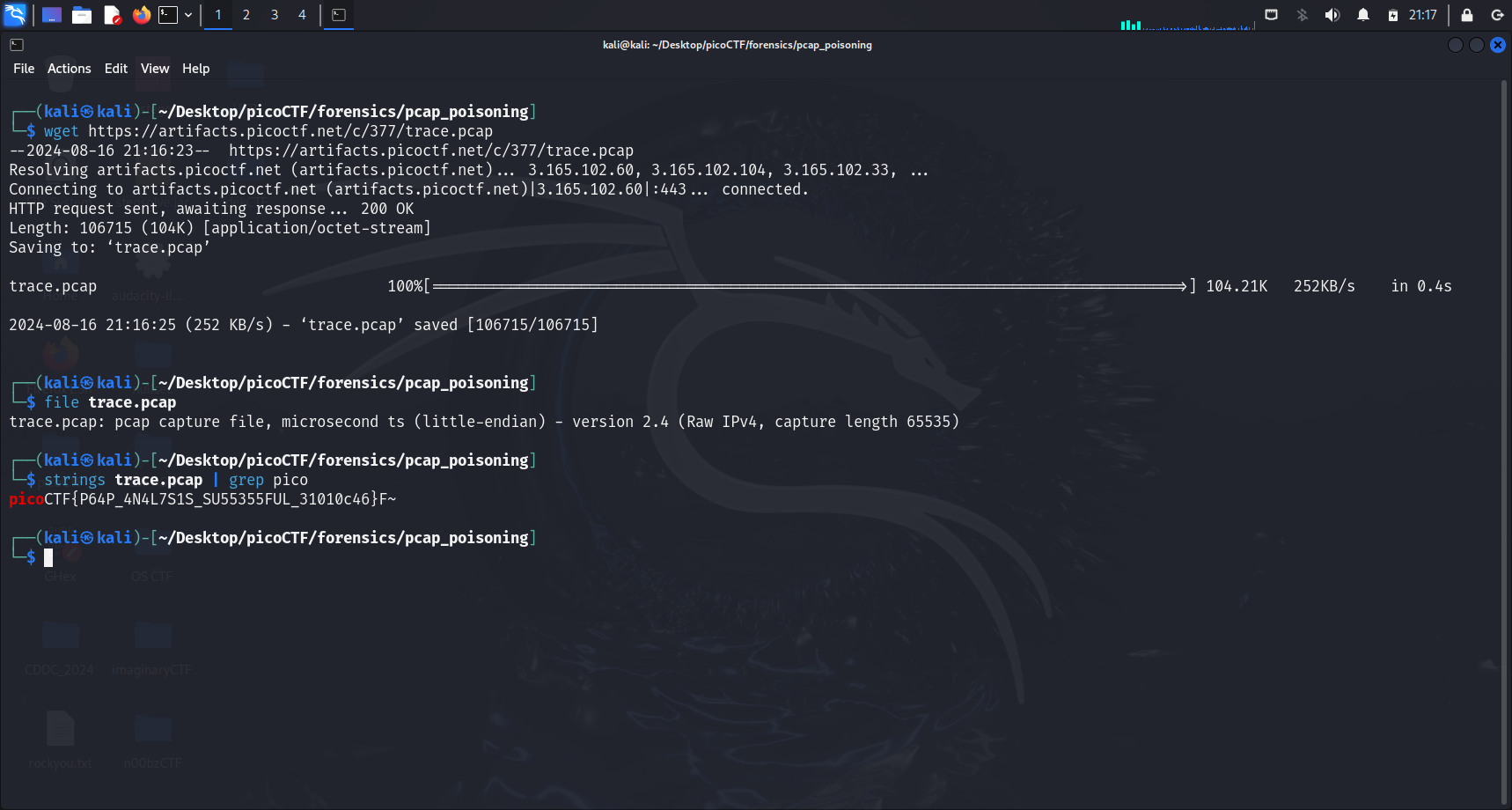
Acquiring the flag using
stringsWe can run
strings <file-name> | grep picoto get the flag immediately. Piping the output of thestringscommand throughgrepwill allow us to filter out line(s) that contain the search term “pico”.
Alternatively, we can use Wireshark for packet analysis.
Using Wireshark
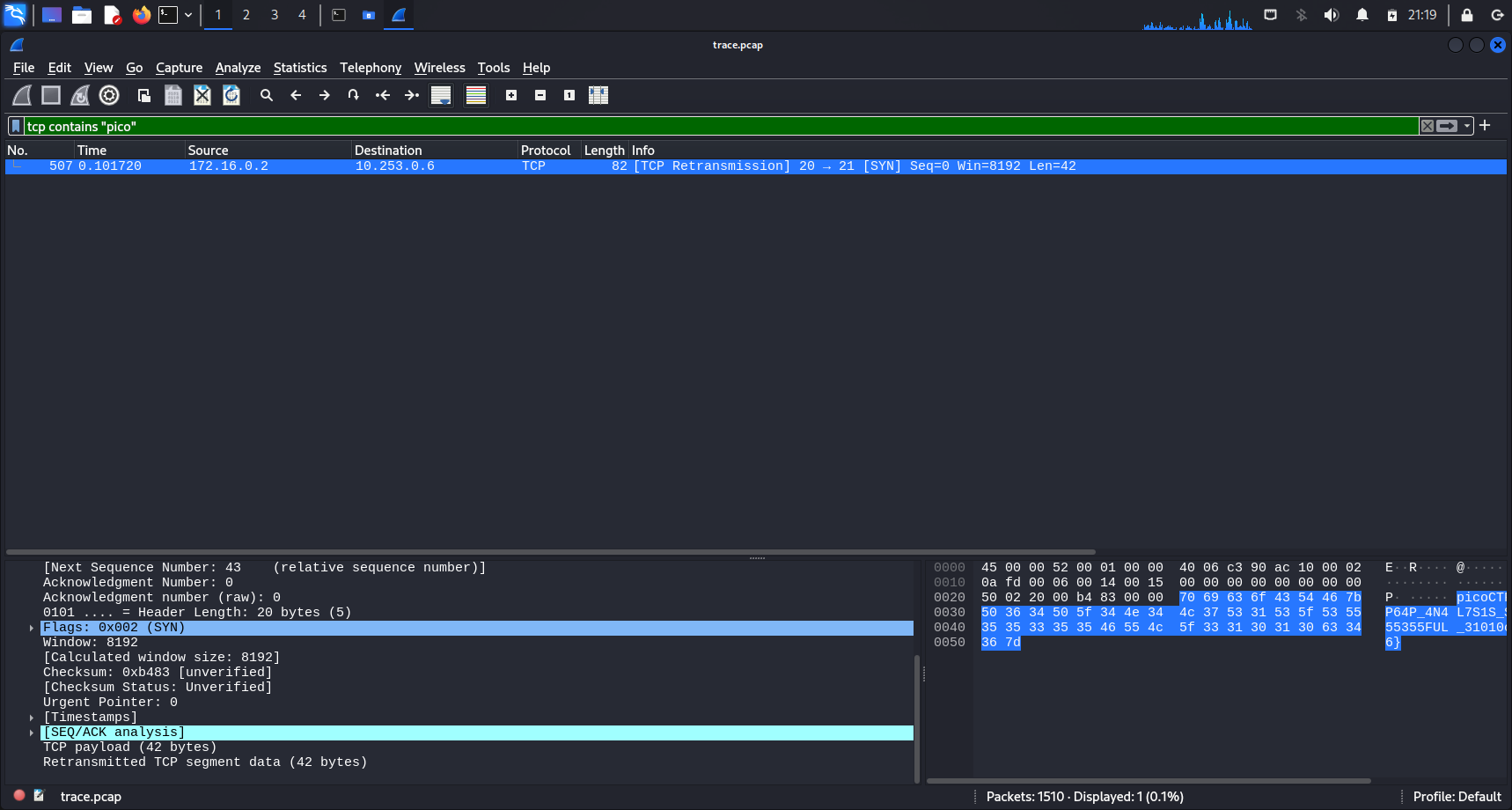
Using the display filter tcp contains "pico", we narrow our search to 1 packet that contains our flag.
Flag
picoCTF{P64P_4N4L7S1S_SU55355FUL_31010c46}