Challenge Description
This seems like an interesting challenge. The name suggests that we will probably have to recursively extract embedded files from the file provided, since this source explains what Matryoshka Dolls are.
Attempting the first binwalk
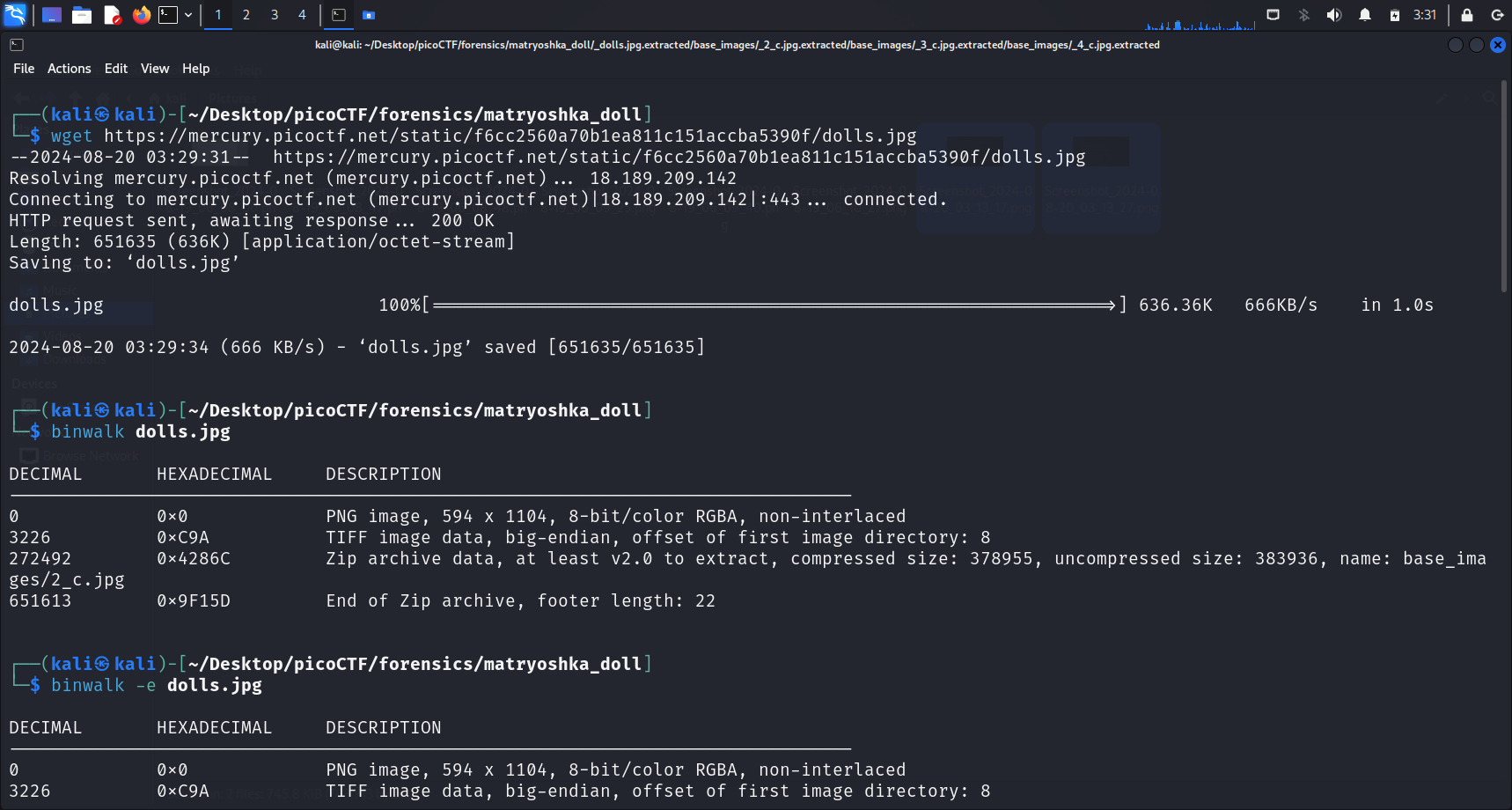
After downloading the file using wget <link>, I tested this hypothesis by first running binwalk. Indeed, there were embedded files that we can extract using binwalk -e <file-name>.
PicoCTF Hint: Wait, you can hide files inside files? But how do you find them?
This once again confirms that we will likely rely on
binwalkfor most parts of the challenge.
Extracted Contents
 After using
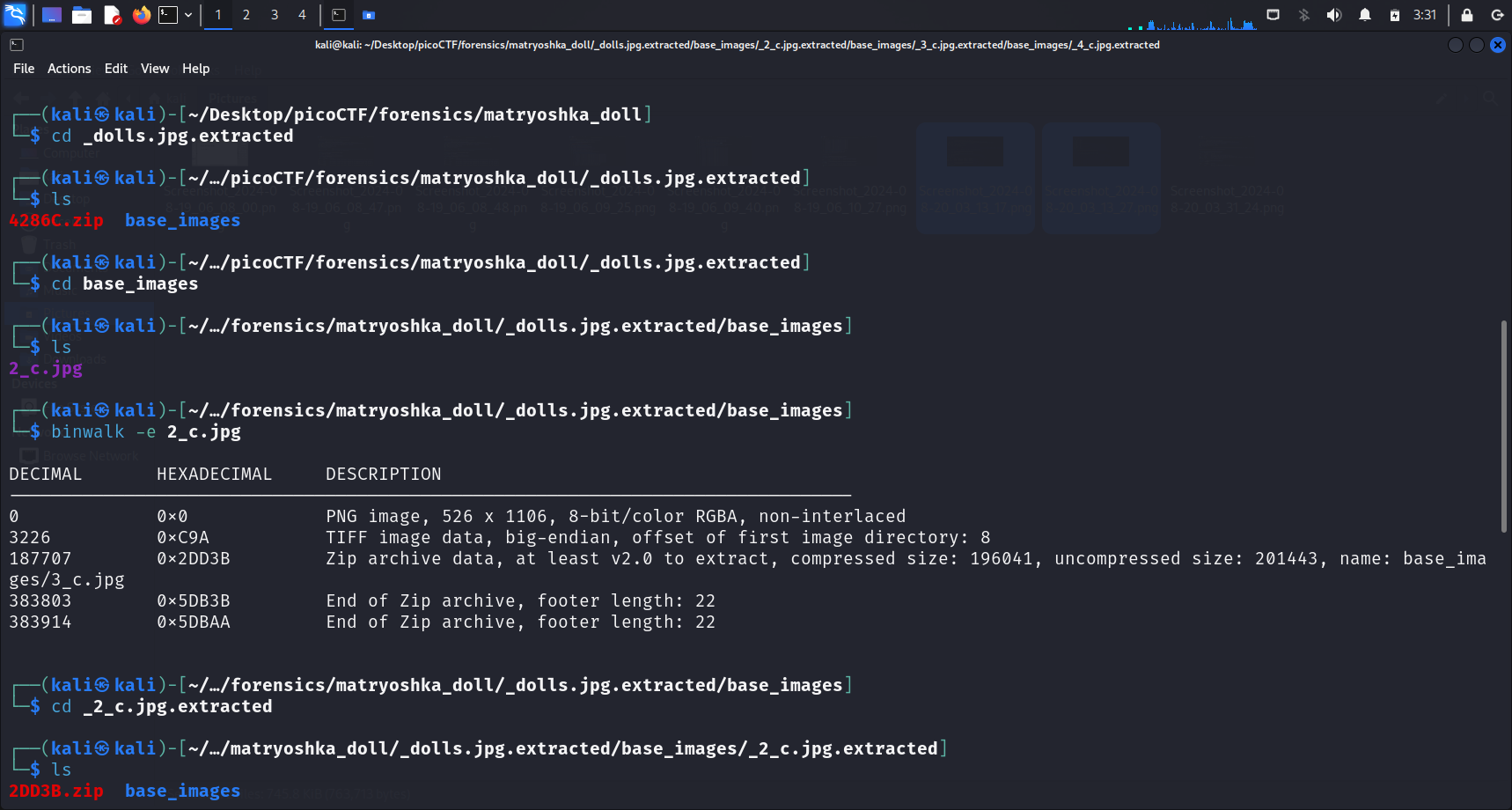
After using binwalk -e <file-name> as described earlier, we realise that a new directory with a zip file and another directory was extracted. Since this challenge was named “Matryoshka doll”, I wasted no time and cd into the base_images directory. A simple ls revealed a file called 2_c.jpg within it.
My Initial Plan
My initial plan was to continuously
cdandbinwalk -eto extract embedded files recursively. If that didn’t work, I would try unzipping the4286C.zipfile and analyse it.
Continuing the Journey
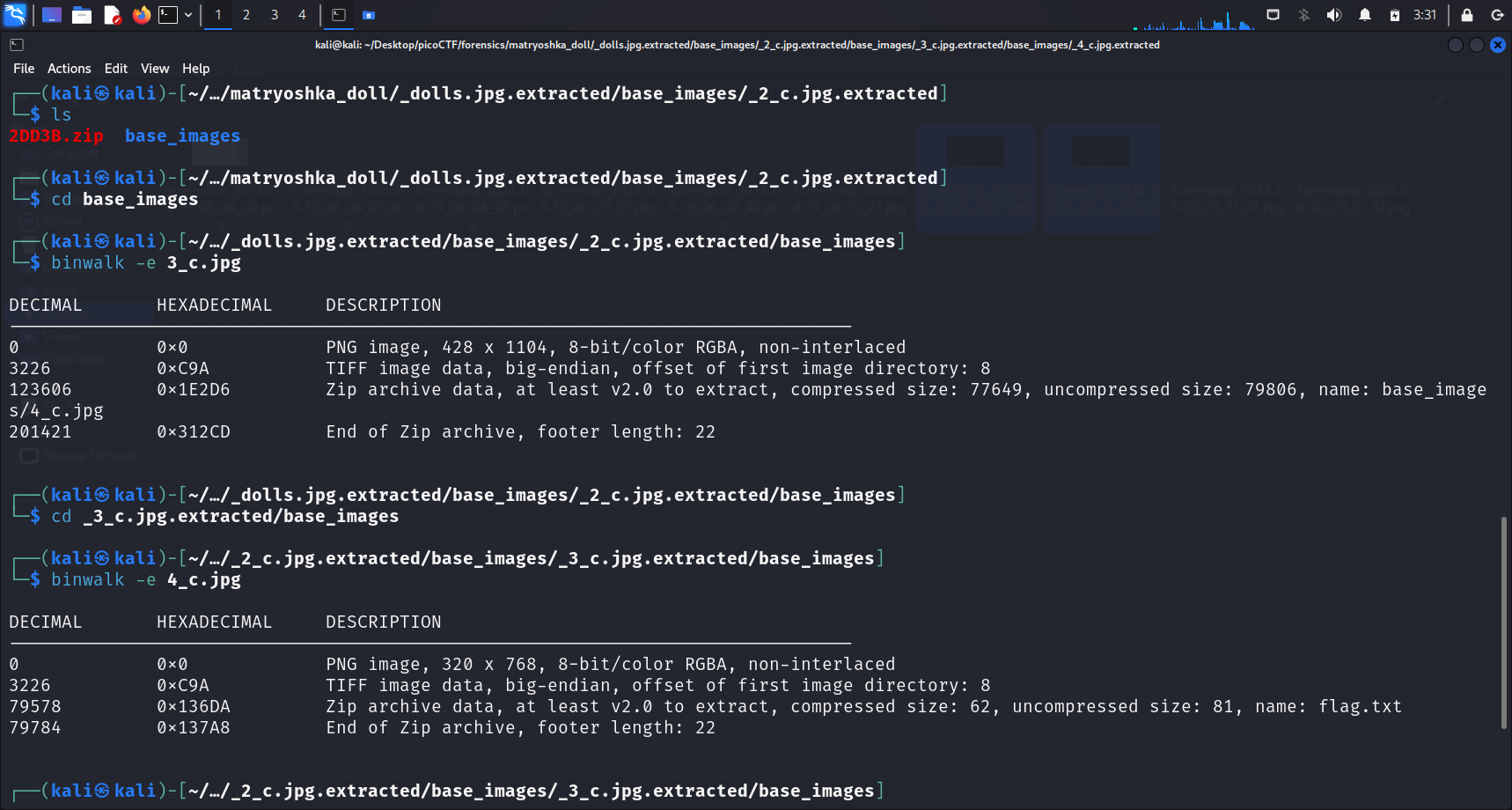
Running binwalk -e on this file allowed us to extract another directory with similar contents. This confirmed that I was most likely heading in the right direction (Matryoshka Doll concept).
Again
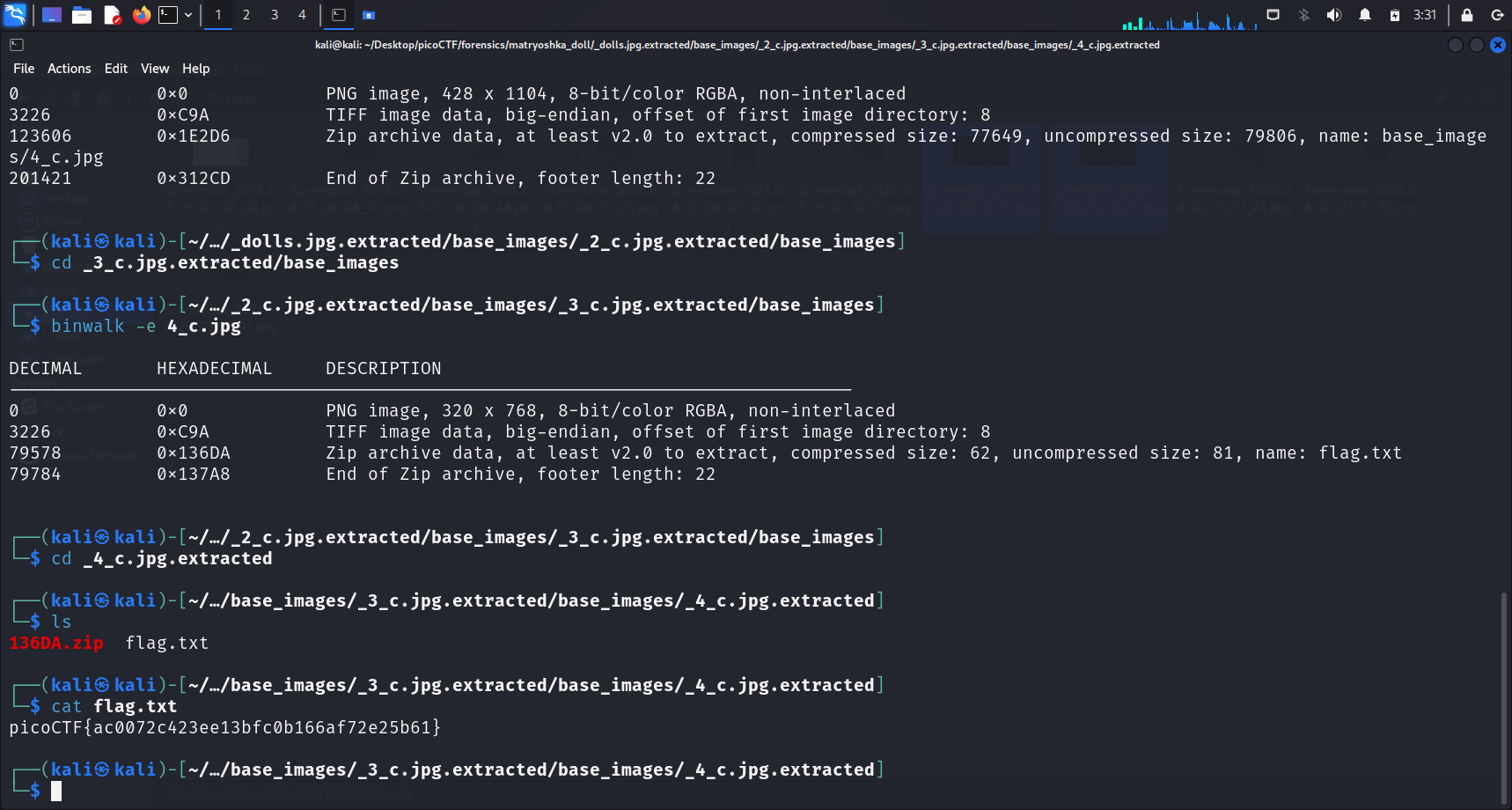 A final
A final binwalk -e on 4_c.jpg extracted a _4_c.jpg extracted directory, but did not extract a base_images directory. Hence I stopped and did an ls to list the contents of the _4_c.jpg extracted directory.
flag.txt
A
flag.txtwas present in this directory. Usingcatrevealed the flag in plaintext.
Flag
picoCTF{ac0072c423ee13bfc0b166af72e25b61}