Challenge Description
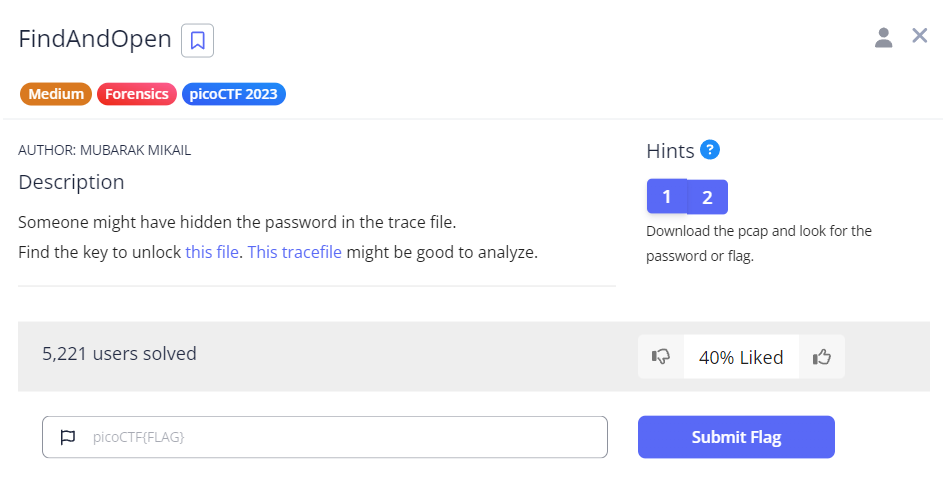
We are provided with a flag.zip file and a dump.pcap file. The flag.zip file is password protected, as displayed below.
PicoCTF Hint: Download the pcap and look for the password or flag.
With the above hint, I ran strings dump.pcap to have a quick glimpse of what’s going on in the pcap file.
Suspicious strings
I identified 5 suspicious strings that are worth paying attention to:
- Flying on Ethernet secret: Is this the flag
- iBwaWNvQ1RGe1Could the flag have been splitted?
- AABBHHPJGTFRLKVGhpcyBpcyB0aGUgc2VjcmV0OiBwaWNvQ1RGe1IzNERJTkdfTE9LZF8=
- PBwaWUvQ1RGesabababkjaASKBKSBACVVAVSDDSSSSDSKJBJS
- PBwaWUvQ1RGe1Maybe try checking the other file
Of the 5 strings, I zoomed into string 3 first. It seems like a Base64 encoded string, with a padding character = at the end. I immediately went to CyberChef to try to decode from Base64.
CyberChef Base64 Decoding
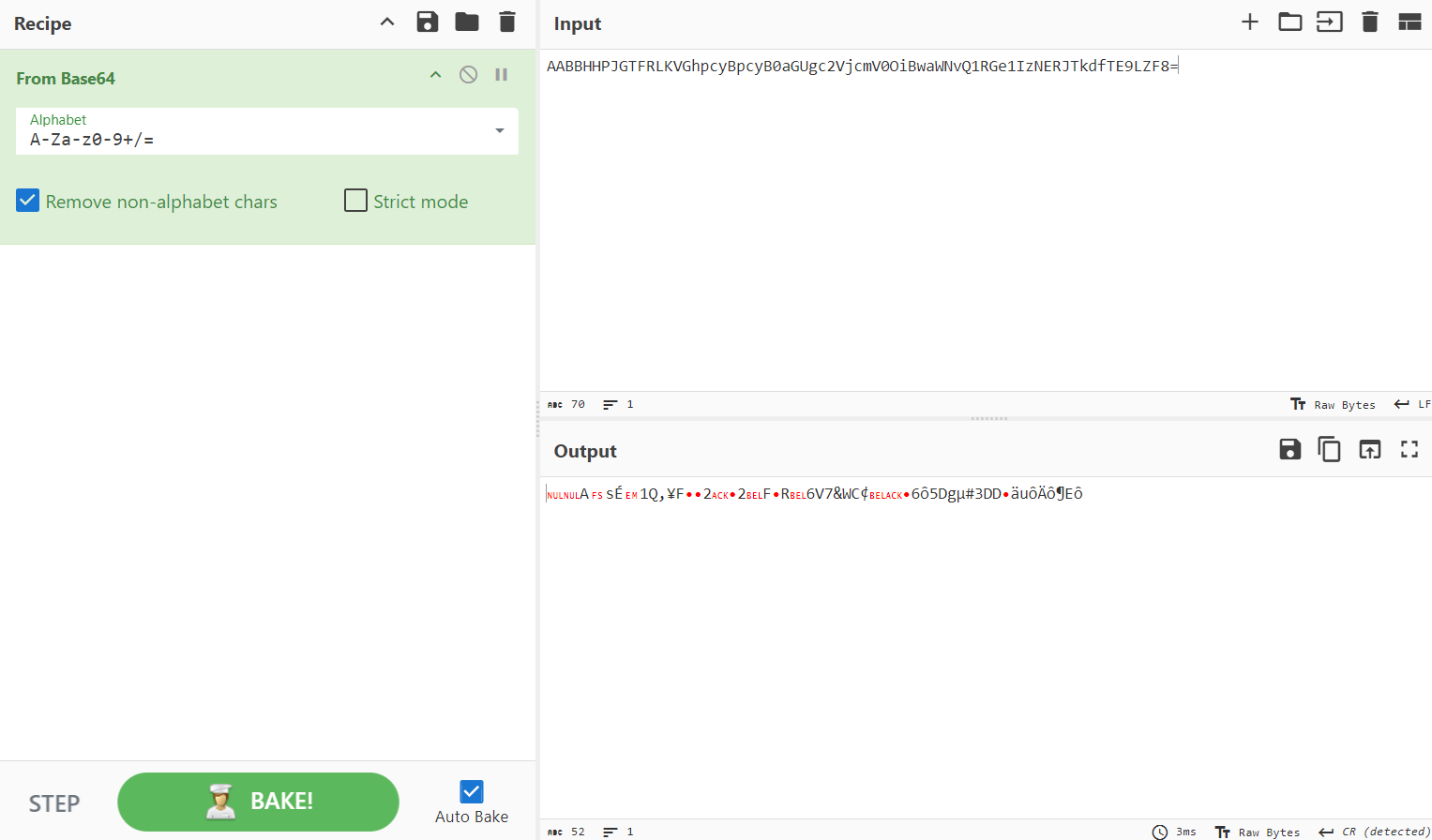
All I got was gibberish. However, I noticed that this string has a length of 70.
How the Base64 encoding process works
During encoding, the Base64 algorithm replaces each three bytes with four bytes and, if necessary, adds padding characters, so the result will always be a multiple of four (What Is Base64? | Learn | Base64, n.d.).
This meant that I will have to delete 2 characters from the input string. I first tried to remove 2 characters from the front.
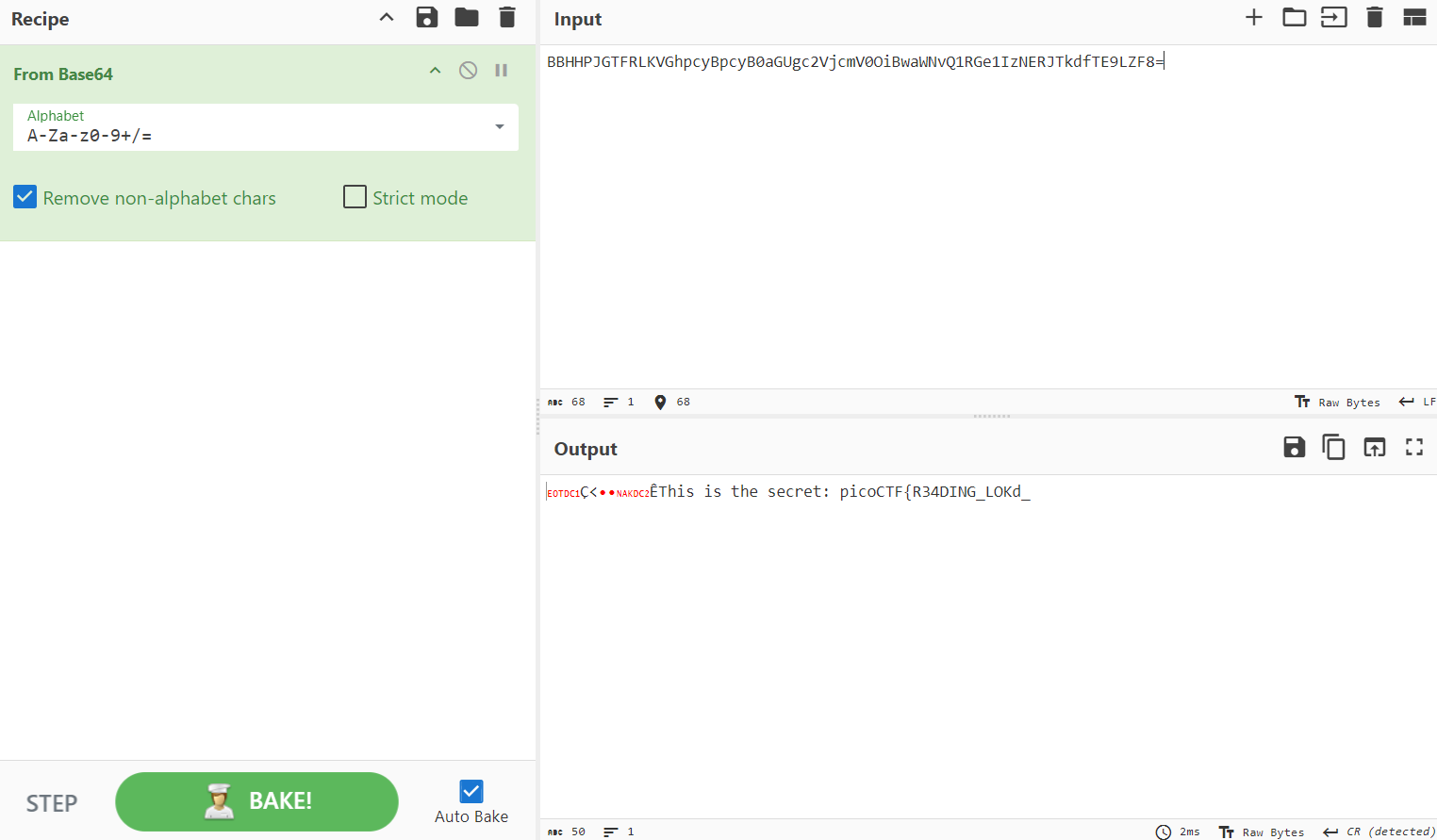
It worked! We now have the flag …right? Well, no. It turns out that this is just half the flag. From string 2 "iBwaWNvQ1RGe1Could the flag have been splitted? " earlier, the challenge hints that the first “flag” we obtain may not be the full one.
I then tried to use our “half flag” to unzip the password protected flag.zip, and obtained the actual flag.
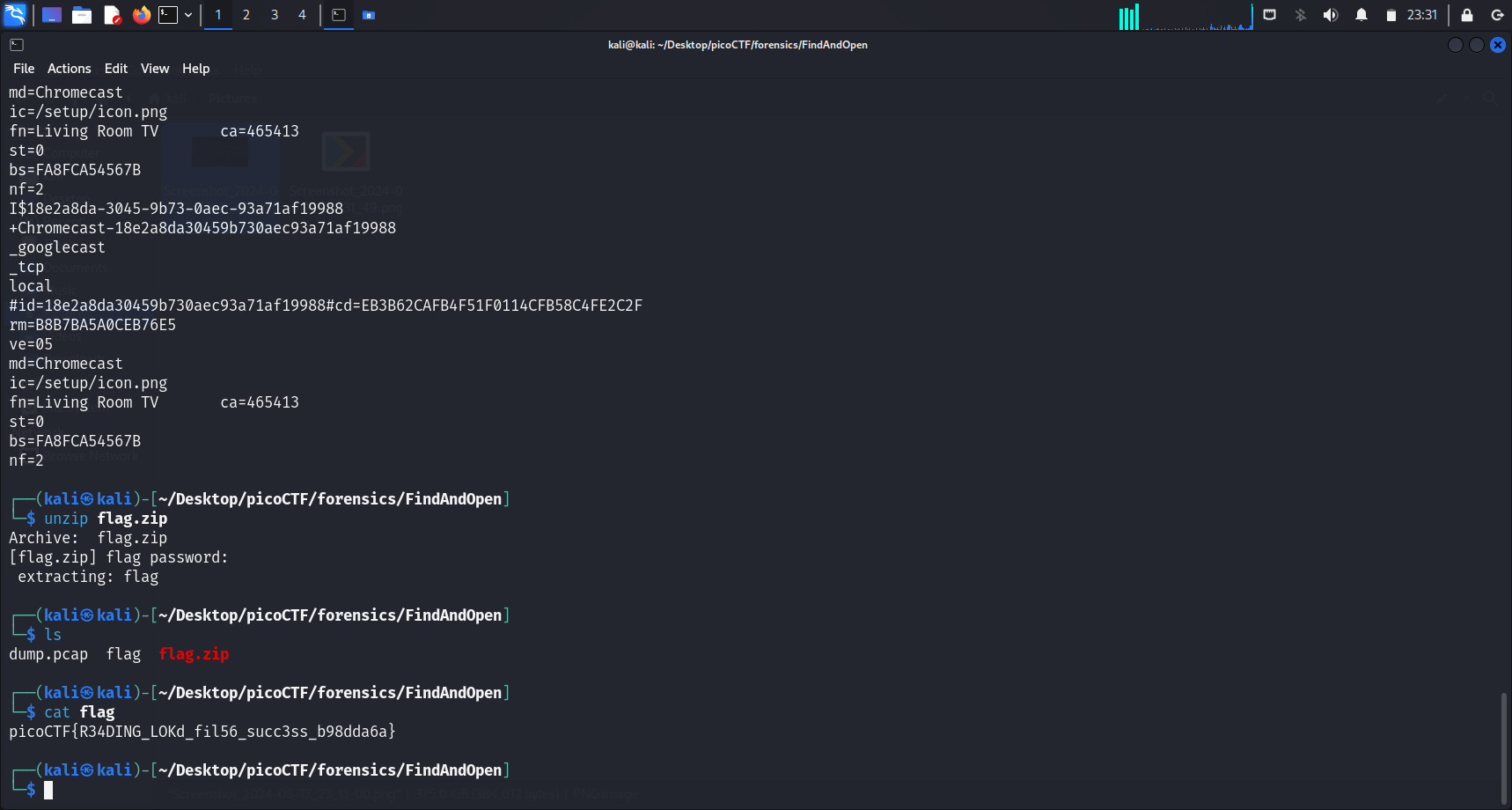
Flag
picoCTF{R34DING_LOKd_fil56_succ3ss_b98dda6a}
What is Base64? | Learn | Base64. (n.d.). https://base64.guru/learn/what-is-base64#:~:text=During%20encoding%2C%20the%20Base64%20algorithm,larger%20than%20the%20original%20data.