Challenge Description
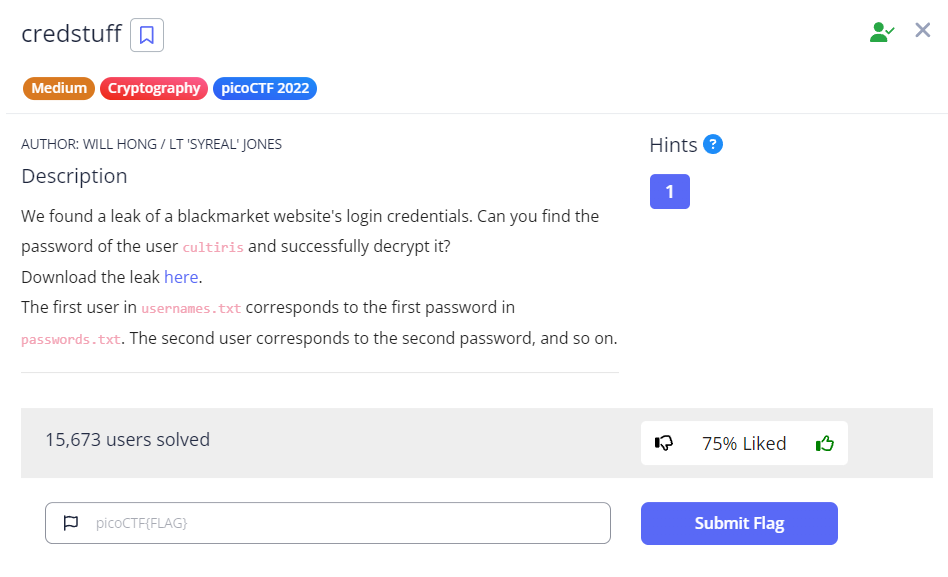
We first begin by downloading the file using wget <link>.
Contents of the Downloaded file
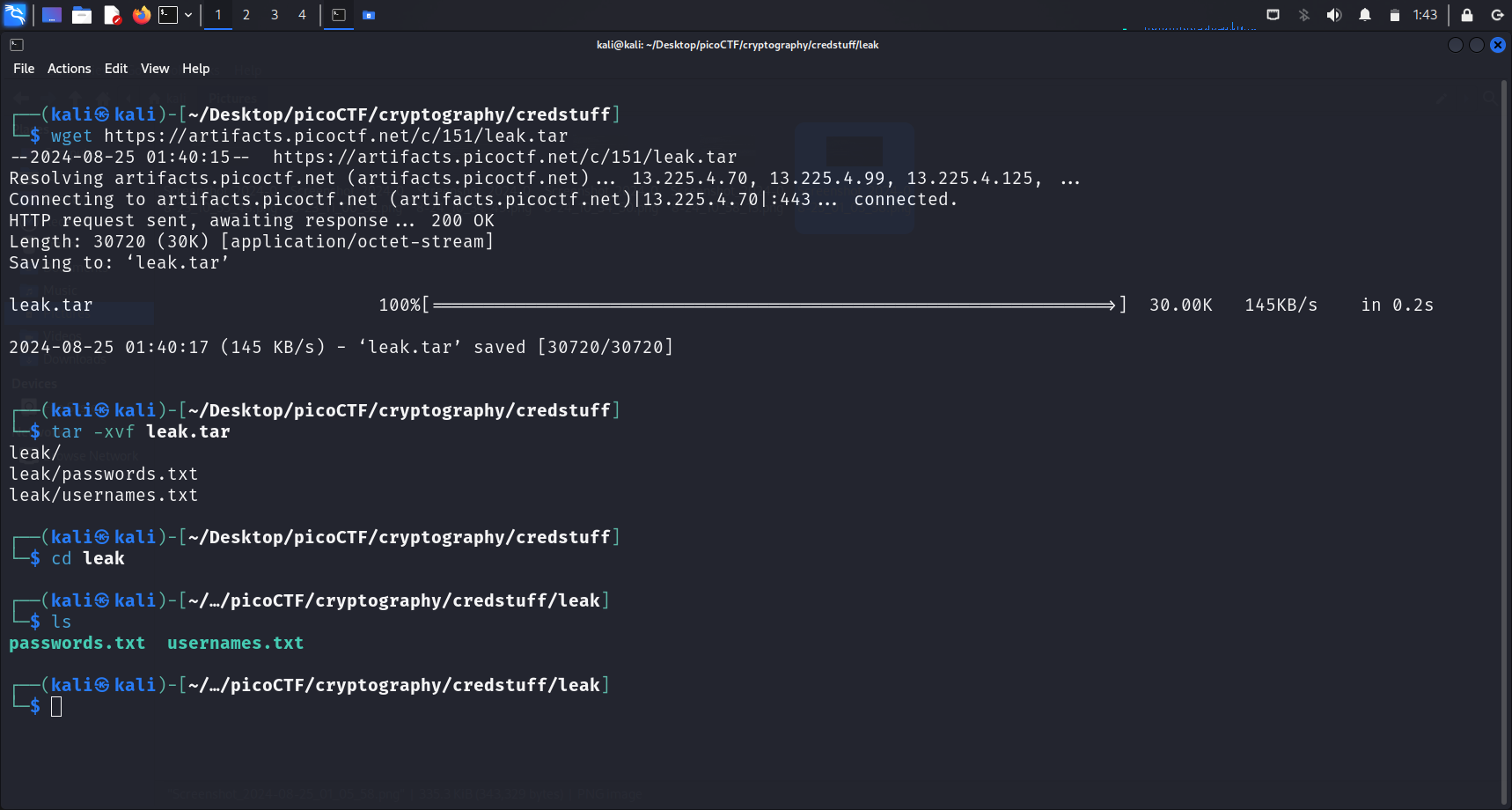 The file provided for this challenge is a
The file provided for this challenge is a .tar file.
What is a TAR file?
A TAR file is an archive saved in the Tape Archive format. It contains multiple files that have been packaged together for easier storage and sharing. Notably, unlike .ZIP files and many other types of archives, TAR files are not compressed (TAR File Extension, 2023).
To extract a .tar file, we can run this command:
tar -xvf < file-name >-x: Extract files from an archive-v: Verbosely list files processed (basically prints the names of the files extracted)-f: Specify archive file name-z: Filter the archive through gzip (for.tar.gzfiles). This is not used for this challenge.
Obtaining the Flag
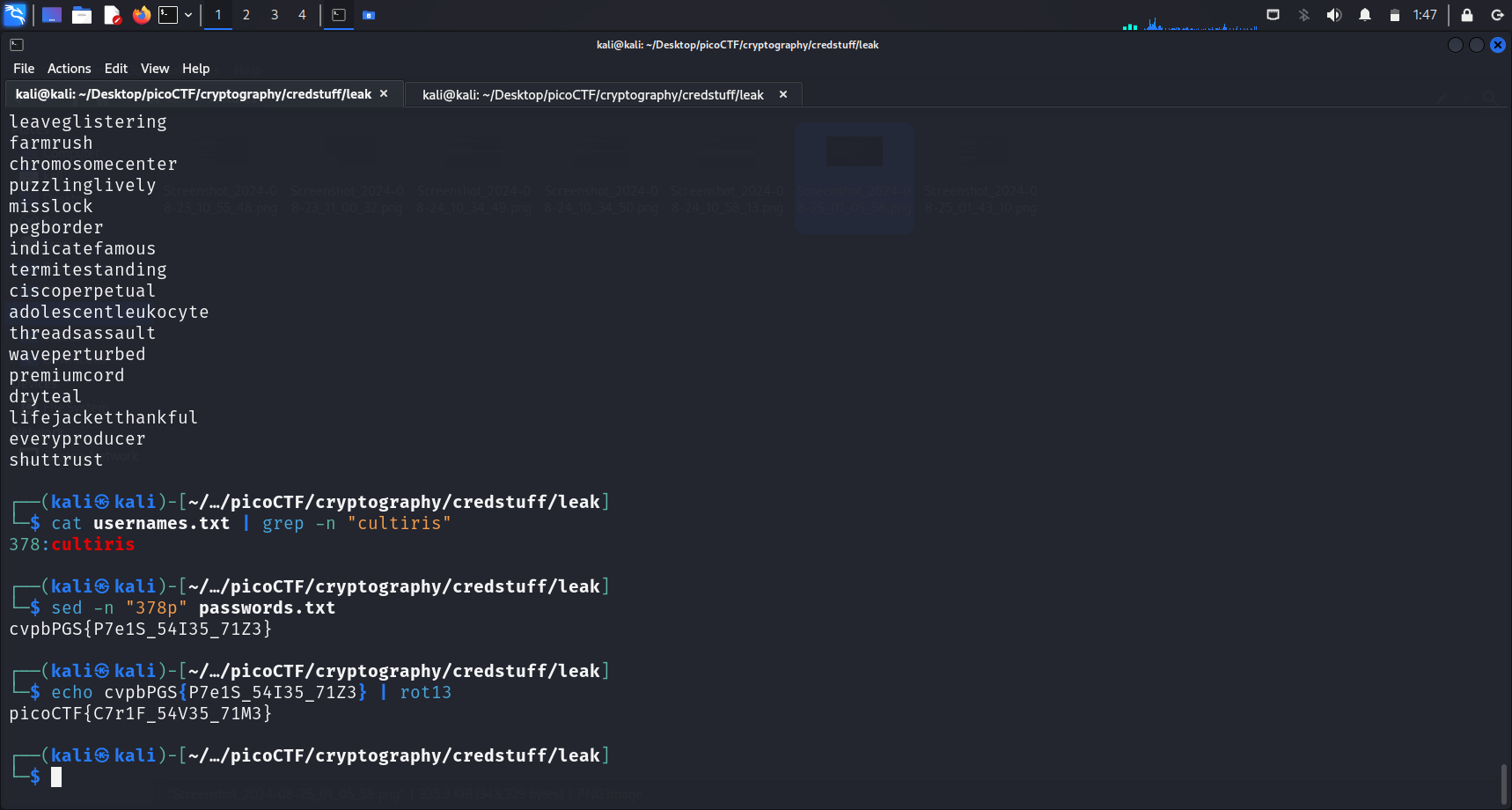
Based on the challenge description, we need to find the password of the user “cultiris” and decrypt it. The first user in usernames.txt corresponds to the first password in passwords.txt. The second user corresponds to the second password, and so on.
The Approach
After running
caton the 2 files,usernames.txtandpasswords.txt, we can see that 1 username and password is displayed on each line for the respective files.This means that we can find the line number of the username “cultiris” in the
usernames.txtfile, and then display the password with the same line number in thepasswords.txtfile.
Finding the line number of “cultiris”
We can find the line number of username “cultiris” in the usernames.txt file by using this command:
cat usernames.txt | grep -n "cultiris"Displaying the password of “cultiris”
We realise that this username is found at line 378. So we will display the 378th line in the passwords.txt file as well, with this command:
sed -n "378p" passwords.txt-n: Suppresses the default output behavior ofsed"387p": Prints only the 378th line
sed
sedis a stream editor for filtering and transforming text. It can be used to edit text files, with its most common use being to replace occurrences of words in a files. This is extremely helpful in situations where a configuration file has a lot of instances of the same word that needs replacing throughout the file.
This command will output this string cvpbPGS{P7e1S_54I35_71Z3}, which looks like it’s been encoded using ROT13. Decoding this will give us the flag.
Decoding the password of “cultiris”
We can decode this using this command:
echo cvpbPGS{P7e1S_54I35_71Z3} | rot13The command echo cvpbPGS{P7e1S_54I35_71Z3} | rot13 prints the string cvpbPGS{P7e1S_54I35_71Z3} using echo, then pipes (|) that output to the rot13 command, which performs a ROT13 substitution cipher on the input string.
Alternatively, we can use tools like CyberChef to decode this string.
Flag
picoCTF{C7r1F_54V35_71M3}
References
- TAR File Extension. (2023, June 15). https://fileinfo.com/extension/tar